Wuzhen Summit Speech | Relaxcloud CEO Bai Yingdong: Large Models Empowering Cybersecurity Operations

From October 13-15, 2023, the 6th Dual-State IT Wuzhen User Conference was successfully held, themed around "Cloud-Native and Large Models Revolutionizing IT Productivity" and "Financial Information Technology Application Innovation Service Assurance." The conference was guided by the ITSS Branch and the Securities and Fund Industry Information Technology Application Innovation Alliance, hosted by the ITSS Data Center Operations Management Group (DCMG), Dual-State IT Forum, and Intelligent Operations National Standards Working Group, with ITSS Media Group and AI Fan'er as co-organizers. More than 500 attendees from finance, central state-owned enterprises, and other industries participated.
Bai Yingdong, CEO of Beijing Relaxcloud Information Technology Co., Ltd., delivered a keynote speech titled "Innovation and Practice of Large Models Empowering Cybersecurity Operations."
Full Speech Transcript
The emergence of ChatGPT marks the arrival of the "strong artificial intelligence" era. Large models are another "new infrastructure" of the digital intelligence era following 5G, big data, and the internet, playing an important role in accelerating the "digital intelligence" transformation and upgrading of industries. Large language models have significant potential in replicating and enhancing human workflows, and also play an important role in cybersecurity industry upgrades.
In our exploration of large models, we discovered two questions: First, should we train large models from scratch by collecting massive data based on general large models? Second, what problems can we solve by applying large models in security industry dialogue scenarios? We position this as a security operations problem.
Fundamental Logic Changes Large Models Bring to Cybersecurity
Overall, the fundamental logic changes that large models bring to cybersecurity are mainly reflected in three aspects:
First, the reasoning capabilities of large models enhance detection capabilities by utilizing the contextual understanding ability of large models to identify threats that humans can discern and threats that traditional feature-based methods cannot easily recognize;
Second, the reasoning capabilities of large models reduce security operations costs. The essence is replacing tasks that require senior security experts to execute—large models can perform complex tasks;
Third, natural language interaction dramatically improves product usability by linking the summarization and synthesis capabilities of large models to traditional security devices, significantly reducing the operational difficulty of security equipment.

Scenario First, Data is King
The fundamental logic changes brought by large models are as mentioned above. In this process, the most important thing is to find scenarios—Scenario First—only by finding scenarios can we solve practical problems. Second is Data is King—data plays a very important role in the exploration process, as it determines the model's capabilities.
At the same time, there are many pain points for large models in security operations. The biggest pain point can be summarized in one sentence: just like security operations, every organization generates at least millions of security data points every day. How to find truly threatening data from millions of data points and address massive alert issues is what we have been exploring.
Potential and Exploration of Large Models in Security
What potential and exploration does the large model have in this area? Our logic for handling security is as follows: call leading security systems across the organization, and use AI for scenario-based integration. This means building an intelligent security operations platform based on large models, training AI large models oriented toward cybersecurity, and achieving integration with current leading security systems (such as XDR, SIEM, EDR, etc.) to empower cybersecurity operations.
Functionally, this model has the ability to deeply understand multi-system data. By comprehensively scheduling API interfaces of various systems, it can achieve intelligent automated processing of security tasks, including but not limited to anomaly analysis, alert noise reduction, threat positioning, assisted attack tracing, response handling, and other capabilities to improve security operations efficiency.
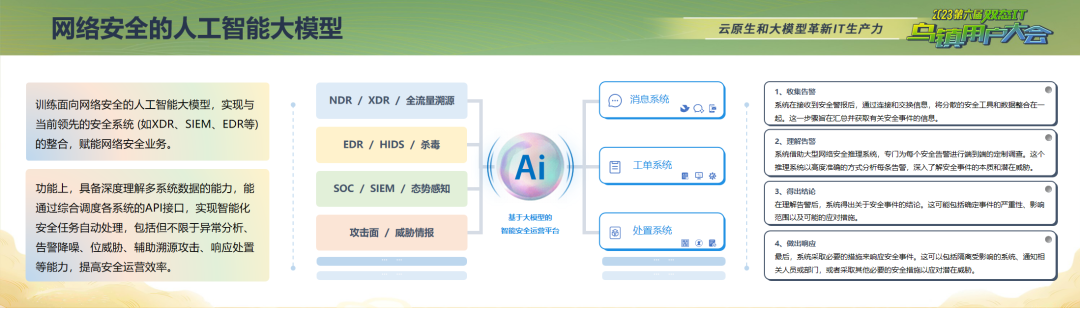
Traffic Monitoring Application Case
Taking traffic monitoring as an example, how do we use large models to solve the problem of excessive traffic and log volume? By calling the traffic monitoring system, viewing alert information, and feeding raw information such as alert fragments and security device judgment information to the large model, we use chain-of-thought mode to guide the large model in determining whether there is actually a danger. Through repeated operations, we finally arrive at comprehensive judgment results, which may include: whether the hacker attack was successful, what to do next, and so on.
Cloud-Based Intelligent Threat Intelligence Operations and Analysis Platform
Speaking of using large models for threat intelligence operations and analysis, we employ a cloud-based intelligent threat intelligence operations and analysis platform. AI runs 24/7 uninterrupted, analyzing every security alert and system log 100% like a security expert. Six AIs playing different roles can respond and handle issues according to standard security handling procedures (SOP), ensuring that security incidents are properly handled and addressed.
In the future, the autonomous evolution capability of L5-level AI will further drive development in the security field. AI will be able to autonomously modify its own configuration and code based on environmental changes, just like humans, achieving capability leaps.
Summary
In summary, the overall approach is Scenario First, Data is King—solving the bottleneck of large models is not about training large models from scratch.
Media Contact Beijing Relaxcloud Information Technology Co., Ltd. Email: lysk@relaxcloud.cn